In a Kubernetes cluster, the primary focus is on orchestrating and managing containerized applications. Kubernetes provides various functionalities like pod scheduling, service discovery, load balancing, and scaling. However, Kubernetes alone does not provide the advanced networking, security, and observability features needed for complex microservices-based applications. This is where Istio, as a service mesh, becomes essential.
Why do we need Istio if Kubernetes already doing all the work?
- Advanced Traffic Control: Kubernetes can route traffic to services, but it lacks the fine-grained control and traffic management features that Istio offers. Istio enables canary deployments, A/B testing, load balancing, and more.
- Security: While Kubernetes provides some security features, Istio significantly enhances security. It offers mutual TLS (mTLS) encryption for all service-to-service communication, as well as access control and authentication features, reducing the risk of unauthorized access and data breaches.
- Observability: Kubernetes provides basic monitoring capabilities, but Istio takes observability to the next level. It collects detailed telemetry data about service behavior, helping operators and developers understand what’s happening in their applications.
- Resilience: Kubernetes does include some resilience mechanisms, but Istio offers more control over retries, timeouts, and circuit breaking, which are essential for building robust and fault-tolerant applications.
- Policy Enforcement: Istio enforces access control, rate limiting, and quotas consistently across all services, which is not a native feature in Kubernetes.
- Network Abstraction: Istio abstracts away many of the complexities of networking, allowing developers and operators to focus on application logic. Kubernetes exposes more low-level network details.
Now you know why Istio is important in a Kubernetes cluster, Let’s deep dive into the Istio, but before we go for Istio let’s first understand What is Service Mesh?
A service mesh is a dedicated infrastructure layer for facilitating communication and managing interactions between microservices in a cloud-native application. In a microservices architecture, where applications are composed of numerous loosely coupled services, a service mesh provides a set of critical capabilities for ensuring reliability, security, and observability.
Now, Let’s relate this back to Istio. Istio is one of the most popular service mesh implementations and provides all the features mentioned above. It works seamlessly with Kubernetes and is designed to enhance the operational capabilities of microservices in a Kubernetes cluster. In essence, Istio simplifies the complexities of managing network communication, security, observability, and reliability in a cloud-native and microservices-based environment.
Architecture of Istio
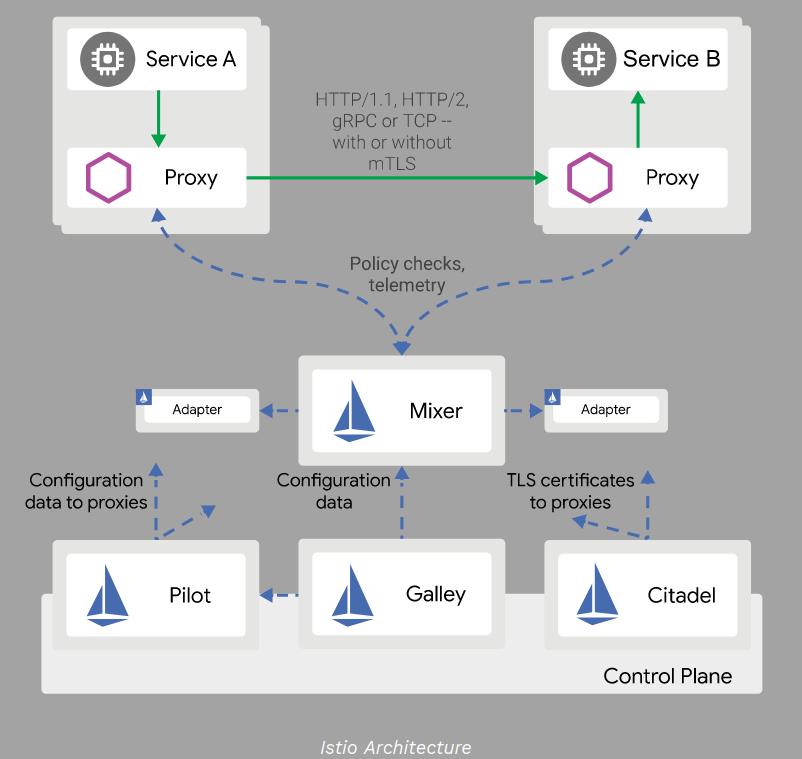
An Istio service mesh is logically split into a data plane and a control plane.
Control Plane
The control plane components are responsible for configuring and managing the data plane (Envoy proxies) and defining traffic routing and security policies.
- Istio Pilot: Pilot is responsible for managing and configuring the sidecar proxies (Envoy) deployed alongside each service in the service mesh. It collects service discovery information, configures routing rules, and distributes them to the proxies. Pilot also provides traffic management features like load balancing, circuit breaking, and traffic splitting.
- Istio Mixer: Mixer is responsible for collecting telemetry data from the sidecar proxies and enforcing access control policies and other desired behaviors. It collects and processes metrics, logs, and traces from the proxies and can integrate with external systems for policy enforcement, monitoring, and analytics.
- Istio Citadel: Citadel provides certificate management and enables secure communication between services through mutual Transport Layer Security (mTLS) authentication. It generates and distributes certificates required for secure communication within the service mesh.
- Galley: Galley validates and processes configuration files in Istio. It ensures the consistency and correctness of configuration across the Istio control plane. Galley receives the configuration files and validates them against the defined schema before distributing them to the appropriate control plane components.
Data Plane
Data plane consists set of proxies(Envoy) deployed as the sidecars along with the container inside a microservice.
- Envoy Proxy: Envoy is a high-performance, sidecar proxy that sits alongside each microservice. The sidecar proxy intercepts all inbound and outbound traffic of the service and acts as a communication channel between services. It provides traffic management features like load balancing, service discovery, and advanced routing capabilities. The sidecar proxy communicates with the control plane to receive configuration and routing rules.
How Istio configured in a Kubernetes cluster
Control Plane Configuration
- Deploying Istio Control Plane: The Istio control plane components, such as Pilot, Mixer, Citadel, and Galley, are deployed as Kubernetes pods. These components are responsible for managing and configuring the data plane sidecar proxies and enforcing policies.
- Installation and Configuration: The control plane components are installed and configured using the Istioctl command-line utility or using Kubernetes manifests. This involves specifying the desired configuration options, such as enabling mTLS, defining routing rules, and setting up access control policies.
- Configuring Pilot: Pilot is responsible for collecting service discovery information, configuring routing rules, and distributing them to the sidecar proxies. The configuration for Pilot includes defining routes, configuring load balancing algorithms, and setting up traffic splitting and fault injection rules.
- Configuring Mixer: Mixer collects telemetry data from the sidecar proxies and enforces access control policies and other desired behaviors. Configuration for Mixer involves defining adapters, configuring policies for telemetry, and setting up quota management and distributed tracing.
Data Plane Configuration
- Sidecar Injection: To configure the data plane, the Istio sidecar containers (usually Envoy proxies) need to be injected into the pods running the application services. This can be done manually by adding the necessary annotations to the Kubernetes deployment manifest or automatically using the Istio sidecar injector.
- Interception of Traffic: Once the sidecar containers are injected, they intercept all of the inbound and outbound traffic of the application containers. They act as the data plane and handle the actual processing and routing of the traffic based on the configuration received from the control plane.
- Proxy Configuration: The sidecar proxies are configured by the control plane components, primarily Pilot. They receive information about the available services, their endpoints, and the routing rules for each service. This information is then used for load balancing, service discovery, routing, and other traffic management features at the proxy level.
- Secure Communication: If mTLS is enabled, the sidecar proxies initiate secure communication between services by establishing mutually authenticated TLS connections. The control plane, specifically Citadel, manages the certificates and encryption keys required for establishing secure communication.
The interaction between the control plane and Data plane happens as follows:
- Control Plane to Sidecar Proxy: The control plane, specifically the Pilot component, collects information about the services, routing rules, and policies from the configuration store. It then distributes this configuration to the sidecar proxies assigned to each service. The configuration is sent to the proxies using a combination of gRPC and the xDS (Discovery Service) protocol, where the proxy subscribes to updates from Pilot to receive the latest configuration.
- Sidecar Proxy to Control Plane: The sidecar proxies, running alongside the services, continuously send telemetry data, such as metrics and traces, to the Mixer component in the control plane. The telemetry data allows for monitoring and observability of the services. Here we can use Prometheus or Grafana to monitor the cluster report. Prometheus is used to collect and store metrics data, including traffic and resource usage statistics. Grafana is used for visualization and querying of Prometheus metrics. You can create dashboards and alerts to monitor the health of your services. The sidecar proxies also report health status and other information to the control plane, providing insights into the state of the services.
It’s essential to note that the control plane and data plane components operate independently of each other. The control plane defines the desired state and configuration, while the data plane (sidecar proxies) implements and enforces this configuration on each service.
In summary, Istio provides a comprehensive solution for managing the complexities of microservices in a Kubernetes cluster. It improves traffic management, enhances security, offers rich observability, and supports the resilient operation of services. For organizations adopting microservices and Kubernetes, Istio has become an essential tool for building, deploying, and maintaining reliable and secure applications.
That’s all for now.
Thank you for reading!!
Stay tuned for more articles on Cloud and DevOps. Don’t forget to follow me for regular updates and insights.

Pingback: Traffic Management of Istio inside the cluster - The CloudOps